
Introduction
Some time ago (July 21 2023), Microsoft released Microsoft Edge management service, a service pretty similar to Microsoft 365 Cloud Policy service, where you can assign policies to every user who logs into Office client app (Edge in this case) using their corporate accounts. This post will explore how to get started using management service, differences from Intune, and how to leverage both services for a better outcome.
Prerequisites
- Microsoft Edge version 115.0.1901.7 or later
- You must be a Microsoft Edge Administrator or Global Administrator to be able to create, edit, and deploy policies.
- You must be using one of the following supported operating systems: Windows 10+ or Windows Server 2016+.
Accessing the portal
The portal can be currently accessed via Admin Portal, but it will soon be coming to Intune under Apps > Policy.
Edge management service or Intune?
Edge management service is like a MAM policy, which follows the user irrespective of the device they log on to (Corporate or Personal), while Intune configuration profiles deploy MDM policies, which require the device to be enrolled, and as we know, most people tend to only MDM enroll corporate devices.
The upside of Edge management service, as mentioned above, is that these policies are supported on Windows Server operating systems as well as personal devices without any management. The downside, though, is that the policies are only applied to the managed profile, and not any other profiles on the browser.
For a quick example let’s say you need to block all browser extensions. If you deploy an Edge management service policy to achieve that on a corporate device and don’t block addition on profiles, the user could easily create another profile and install whatever extension they like. On the other hand, if you were to block all extensions via an Intune policy, any exception required would need to be deployed and targeted via Intune (which at scale might present some management overhead) and only Intune enrolled devices would receive these policies.
Edge management service and Intune
Here is how you can combine Edge management service and Intune to block all extensions on managed devices and allow exceptions per request based on user feedback.
Creating and assigning policies
- Create a group of users to pilot the policies.
- Navigate to Intune Portal and create a new Windows 10 and later Settings catalog policy, give it a name (mine is called Block all Edge Extensions), search for Control which extensions cannot be installed, add the setting and populate the first field with an ‘*’ so all extensions are blocked and deploy to the group created in step 1.
- Navigate to and click Create configuration profile.
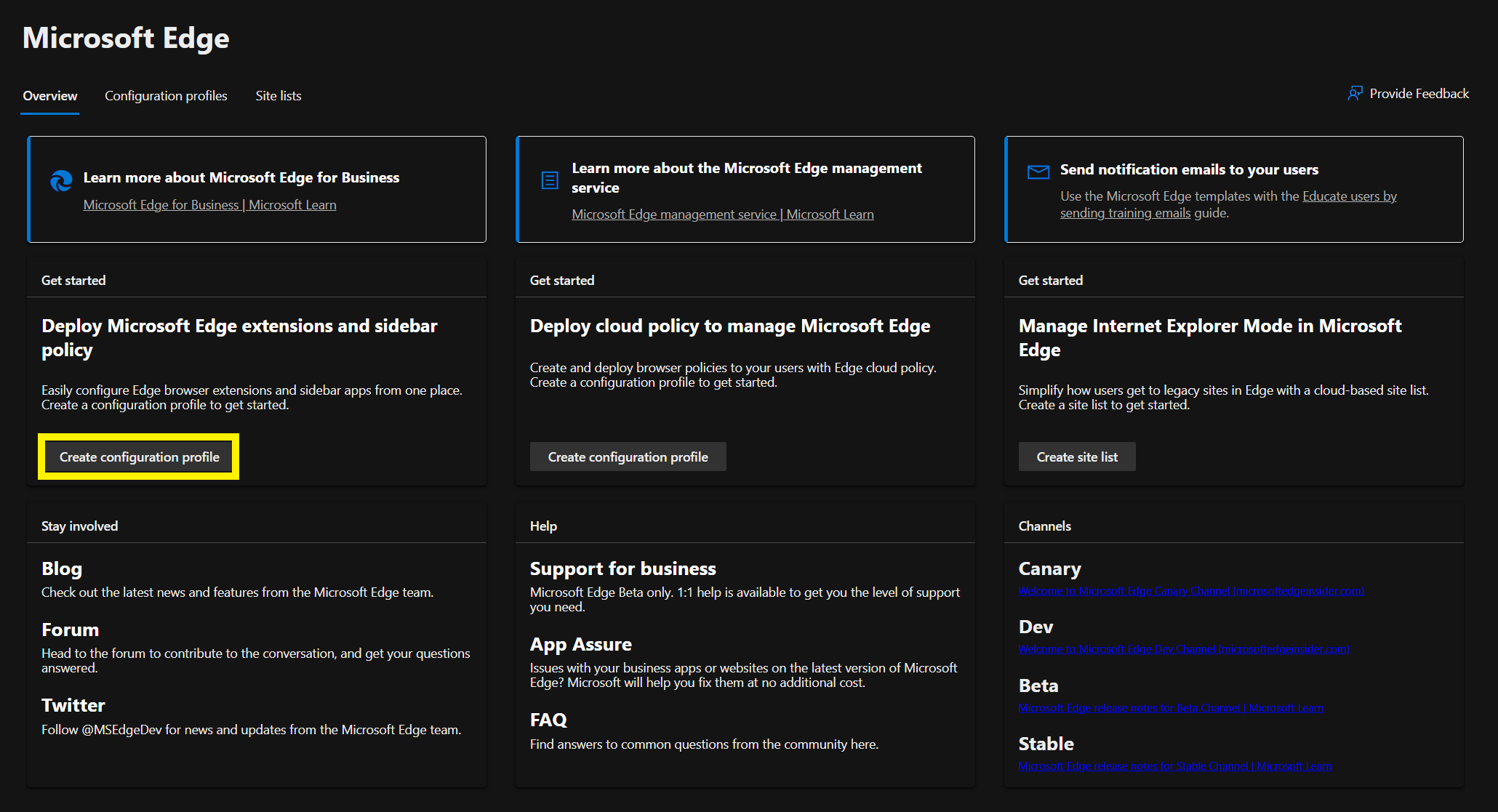
- Give it a name and click select.
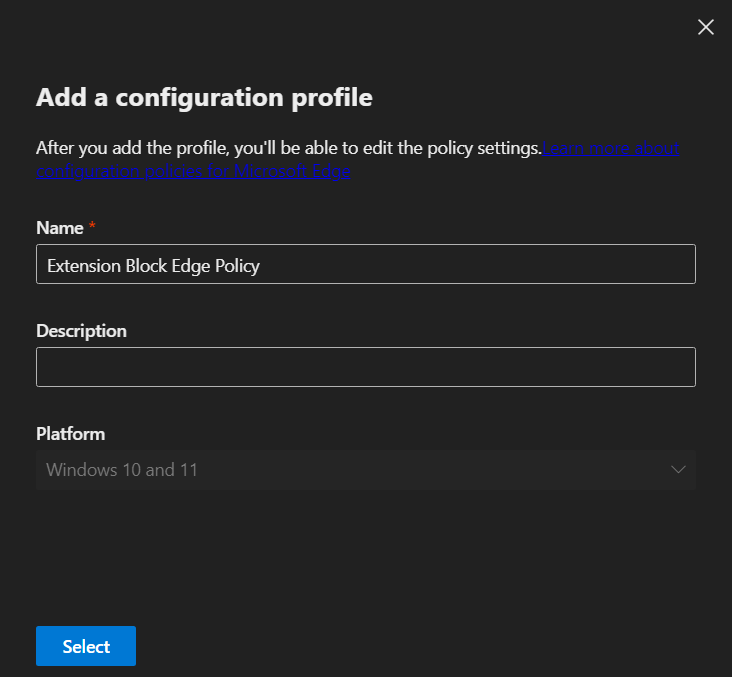
- Once created, navigate back to Configuration profiles and click the policy created.
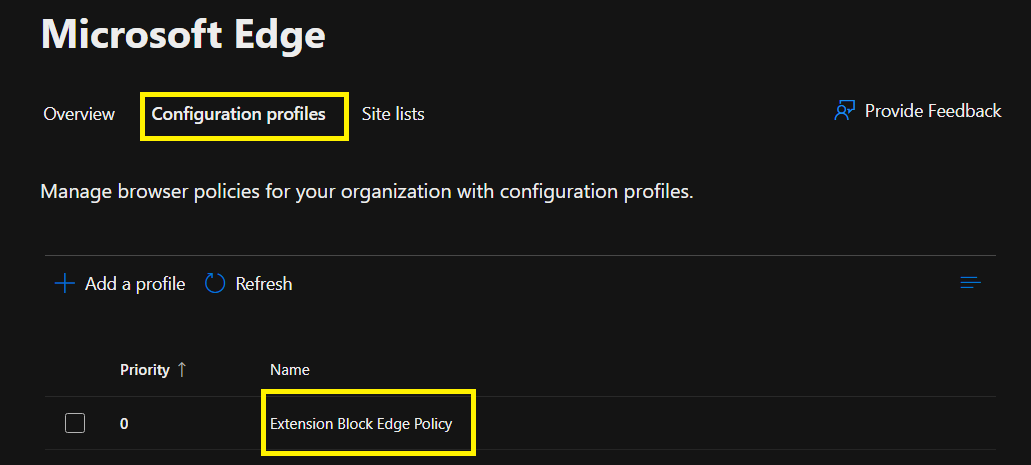
- Inside the policy there are 3 areas, Policies, Extensions and Group assignment. For this example, we will be using Extensions.
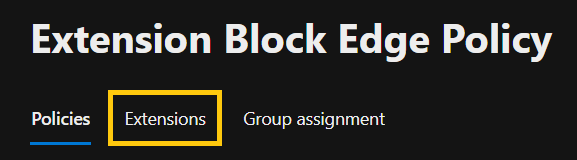
- Inside extensions, click Manage extensions.
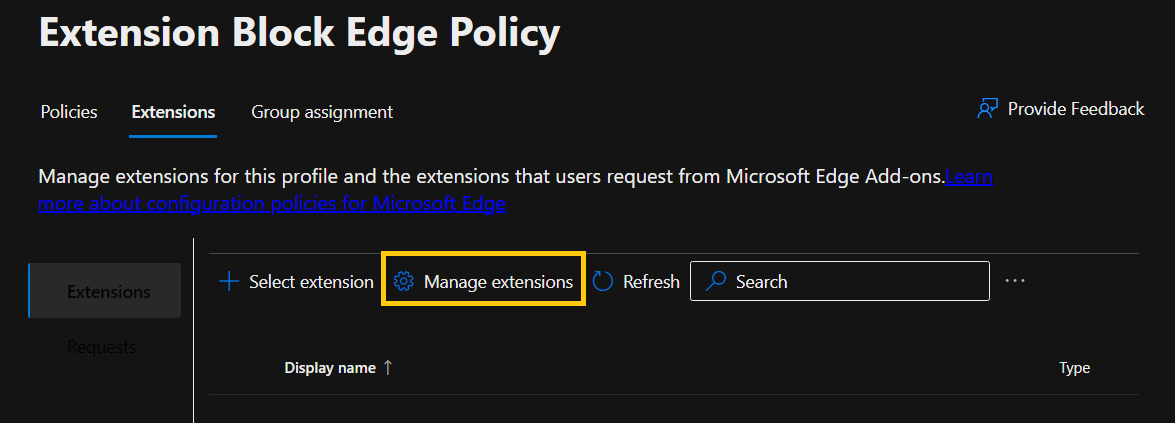
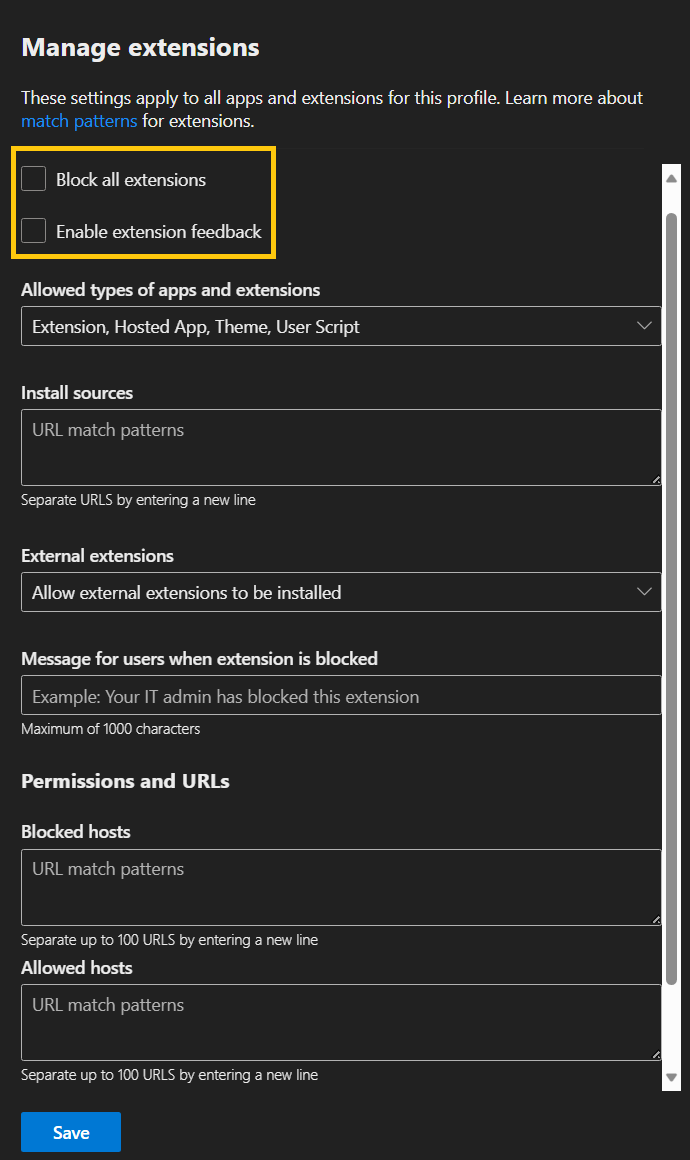
- Inside Manage extensions, you can configure many restrictions, but for this example let’s just select the two first checkboxes and save.
- Now, go to Group assignment and assign the group created in step 1.
Blocking results
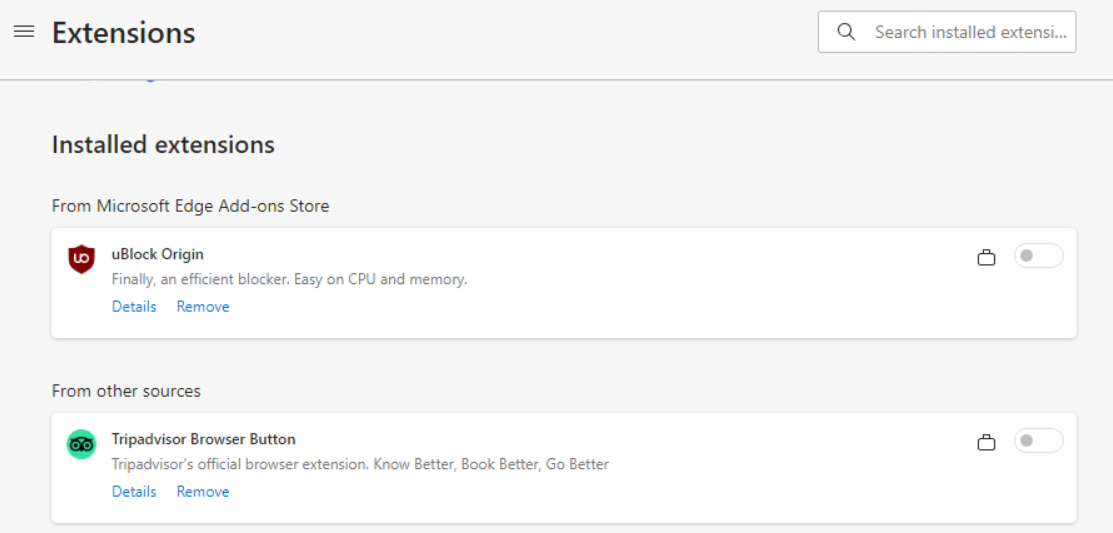
To test the discussed scenario, I’ve used an Intune managed device with 2 extensions installed, Ublock Origin and Tripadvisor Browser Button.
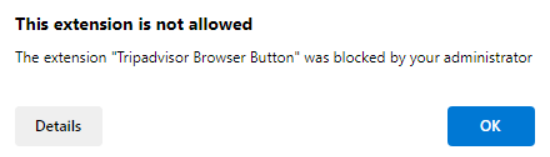
When the Intune policy was assigned first, the user got a pop notification for only one of the extensions saying the administrator blocked it.
When the Edge management service policy was assigned first, no pop, the extensions just vanished from the main windows, but in both instances, they could be seen under extensions as managed and disabled.
Enable extension feedback
Enable extension feedback only works with Edge Add-ons (extensions from the Microsoft Edge store). If you are required to support Chrome Web Store extensions you will need to install them manually. For Edge Add-ons, when a user tries to install one, they will have the chance to provide a business justification.
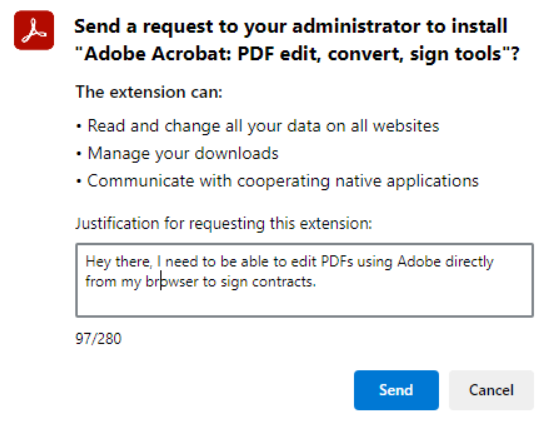
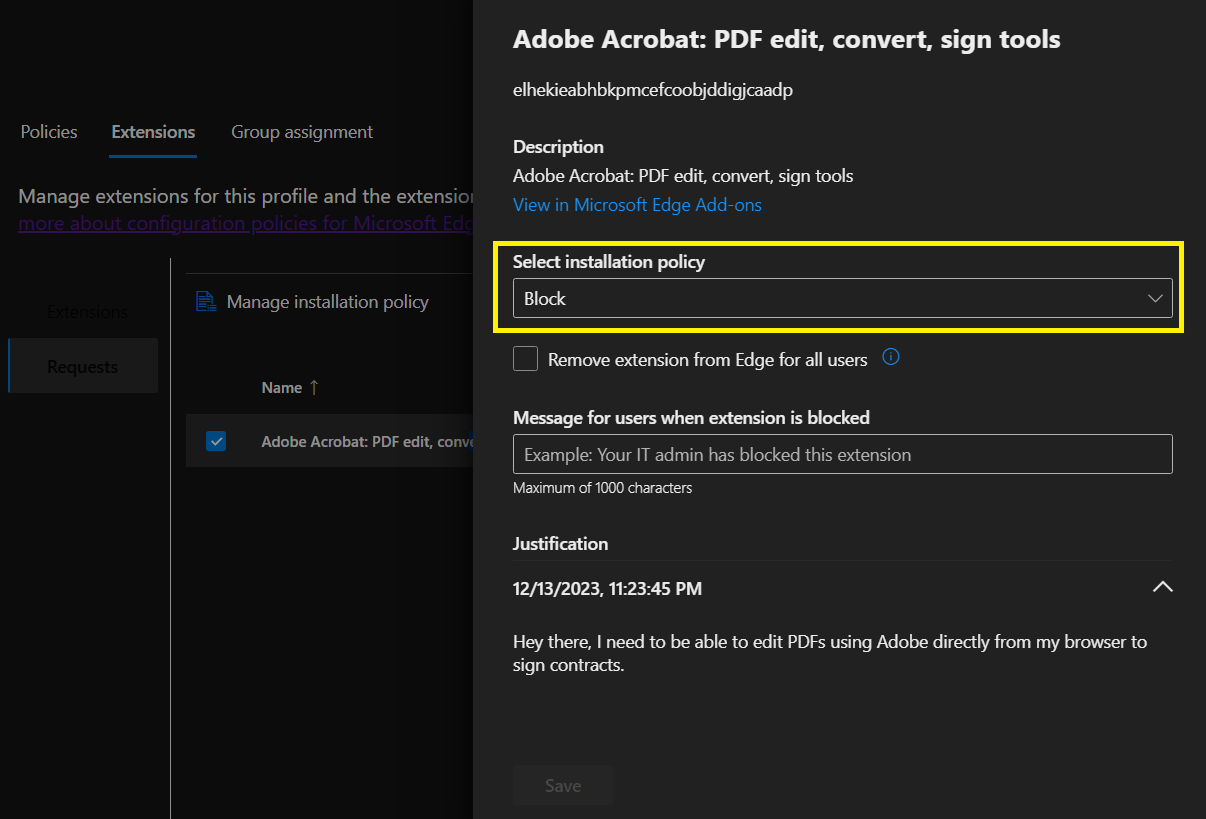
Once the user submits the request, back at the Admin Portal, under requests you can find all the add-on requests, how many were requested, drill down into justifications, and decide which action you want to take.
Bonus tip
When you initially block all extensions, they will not be removed from users’ profiles, only disabled. So, for a user to be able to request that extension via the Feedback portal, they need to remove it from their profile and re-add it, thus triggering the feedback process. This process is broken in my opinion and will generate a lot of unsatisfied users.
Browser Extension Reporting
I’ve recently created a PowerShell Module to help report on all extensions installed on a given device (for all users and all main browsers like Edge, Chrome, and Firefox).
If you would like to learn more about it please visit Reporting on installed browser extensions. By using this module you could easily report on all the extensions installed across your company and revise what is in use by whom before deciding on what should be blocked and what should be allowed.
Hope that was informative and thanks for reading.
Comments