
Introduction
This post will talk about my latest PowerShell module BrowserExtensionReporting, which helps with reporting on installed browser extensions for users. Many security frameworks define that browser extensions should be allowed listed only, but following that requirement without understanding what is already out there is quite challenging. Hopefully, this PowerShell module can help with that initial (and why not ongoing) reporting of your browser extension estate.
Installation
The module is published to PowerShell Gallery and has no dependencies so installation is simple
Install-Module -Name BrowserExtensionReporting
Parameters
This section will explore all the parameters of the only available function (Get-BrowserExtensionInfo)
Browser
If not specified, this parameter will default to all supported browsers currently (Chrome, Edge, and Firefox). Edge and Chrome have multiple entries for each channel (Beta, Canary, and Dev) because they store different channels in different folders, Firefox uses the same profile folder for all channels, and it controls at a profile level which profile is connected to each channel.
If a specific browser is required here are the possible values
- Chrome
- ChromeBeta
- ChromeCanary
- ChromeDev
- Edge
- EdgeBeta
- EdgeCanary
- EdgeDev
- Firefox
Examples
Get-BrowserExtensionInfo -Browser Edge,Chrome
Get-BrowserExtensionInfo -Browser Edge,EdgeBeta,EdgeCanary,EdgeDev
Get-BrowserExtensionInfo -Browser Chrome,Firefox
User
If not specified, this parameter will default to currentuser, the user executing the function. Any other options must be run with a user that has administrative privileges (you cannot read other users’ files and folders without it).
The current options are:
| Parameter | Info |
|---|---|
| AllUsers | Combination of LocalUsers, VirtualUsers and EntraUsers |
| LocalUsers | All accounts under HKLM:\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProfileList with a SID of S-1-5-21-* |
| VirtualUsers | All accounts under HKLM:\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProfileList with a SID of S-1-5-110-* |
| EntraUsers | All accounts under HKLM:\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProfileList with a SID of S-1-12-* |
| CurrentUser | The current user running the function. |
| LoggedOnUser | The active account logged on to a computer. This was created to support programmatically capturing users on Remote Sessions (such as Windows 365, AVD, and DevBox) |
| Other | Once selected, this option will prompt for a username and it should match the profile name. |
Note: Note this parameter does not support multiple entries
Examples
Get-BrowserExtensionInfo -User LoggedOnUser
Get-BrowserExtensionInfo -User EntraUsers
Get-BrowserExtensionInfo -User Other
Please provide user name: **user1**
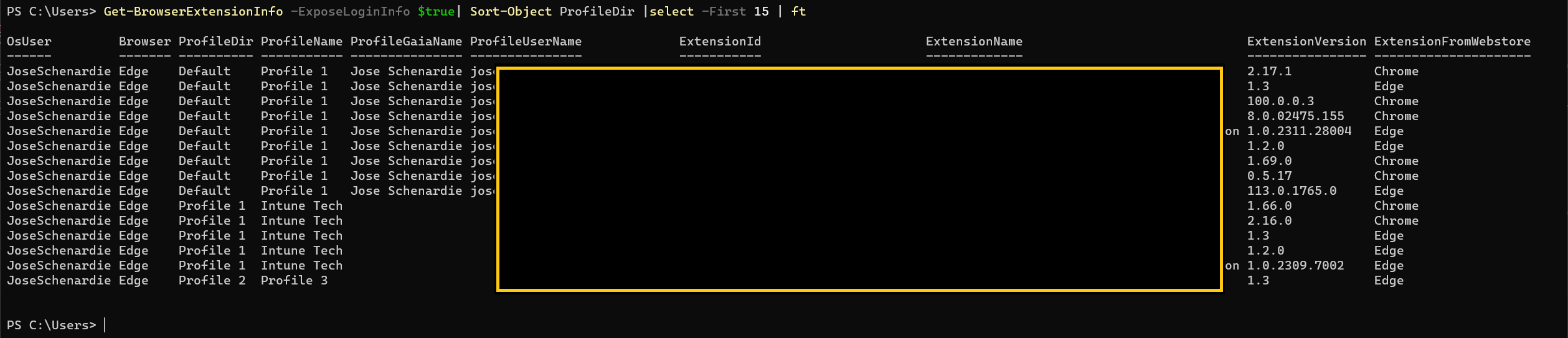
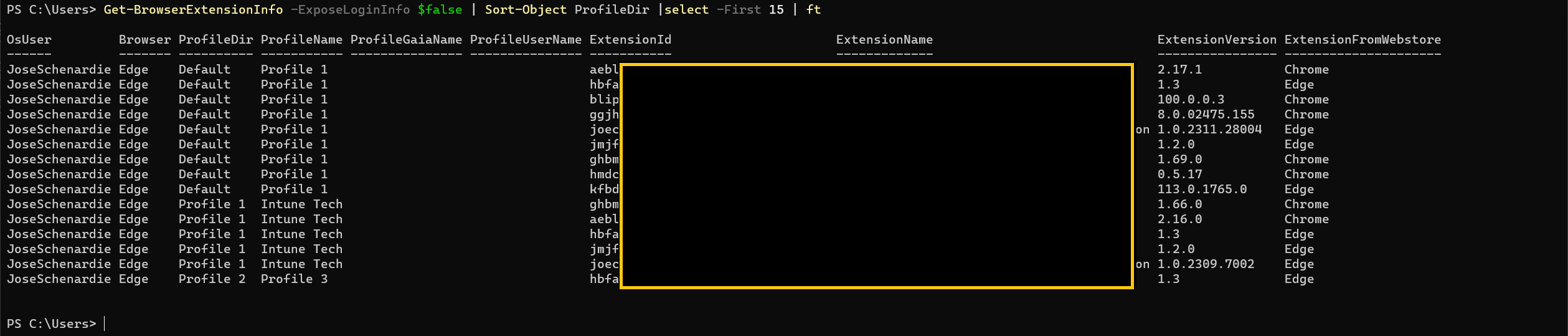
ExposeLoginInfo
The main function has the option (turned off by default) to collect usernames (ProfileGaiaName) and e-mails (ProfileUserName) for profiles where the users signed in. For compliance reasons, harvesting such information might not always be a good idea. If the user has logged on with a personal account, their username and e-mail for that account will be exposed. To enable this function set the parameter to $true.
Examples
Exposing Login Info:
Hidding Login Info:
Other information
Note: Some properties might not show depending on which browser select. ExtensionInstalledByDefault and ProfileGaiaName are exclusive to Chromium browsers, so they will always show empty on Firefox.
Special Thanks
Once again, I’d like to thank Helge Klein for ceding many functions used on this module which are based on his script for uberAgent
Hope that was informative and thanks for reading.
Comments