
If you have been using Microsoft PIM (Privileged Identity Management) to provide just-in-time access to company resources with approval flows you must be aware that the only notification option currently is to send e-mails to approvers. What if you could take those notifications and shared them with the approvers on Microsoft Teams or Slack?? This post will explore how we can do just that.
Challenge
This flow is a little different from the previous one shared in this blog (here and here). PIM is divided in three categories, Entra Roles, Azure Resources and Groups. Each one of those requires different permissions and endpoints (well Azure Resources doesn’t even use Graph, but ARM API). We are currently at the third iteration of PIM API and things honestly don’t look any easier.
Luckily, another single endpoint has all the elevation requests and provide a read only scope: AuditLog.Read.Al Once I found that out, the rest was pure logic, which is available below.
Now, when dealing with Entra ID Logs, you should know there are factors to be considered regarding the latency of that data showing up on your console / Graph. Because of that, the logic app introduces a delay of 5 minutes (on my experience logs never take longer than that to populate, but if you experience higher delays you can always change those values) when querying Graph, so for example if you run it at 8:40, it should bring you all the requests between 8:30 and 8:35.
Pre Requisites
- Azure Subscription with enough permission to create the resources required - Logic App with system-managed identity and Key Vault to securely store the webhook information
- Global Admin or Cloud Application Administrator access (one time only) - give the logic app managed identity access to query Intune
- Enough access to Slack / Teams to create and configure webhooks - allow the logic app to send notifications to your favorite IM tool
Architecture
This solution comprises three Azure resources, a logic app which is where all the logic for the alerting happens. A key vault which is a “safe” where we securely store the webhook link (with this link anyone can send messages to a specified channel, hence why we want to secure it), and an API connection which allows the logic app to read information (the webhook) from the key vault.
The logic app runs on a schedule, query pending PIM elevation requests via Graph API, and upon finding new requests it generates a message that is then sent via webhook to the preferred IM tool (Teams or Slack).
Deploying
Slack Option
Teams Option
The above links should take you to the custom Azure template windows like the one shown below
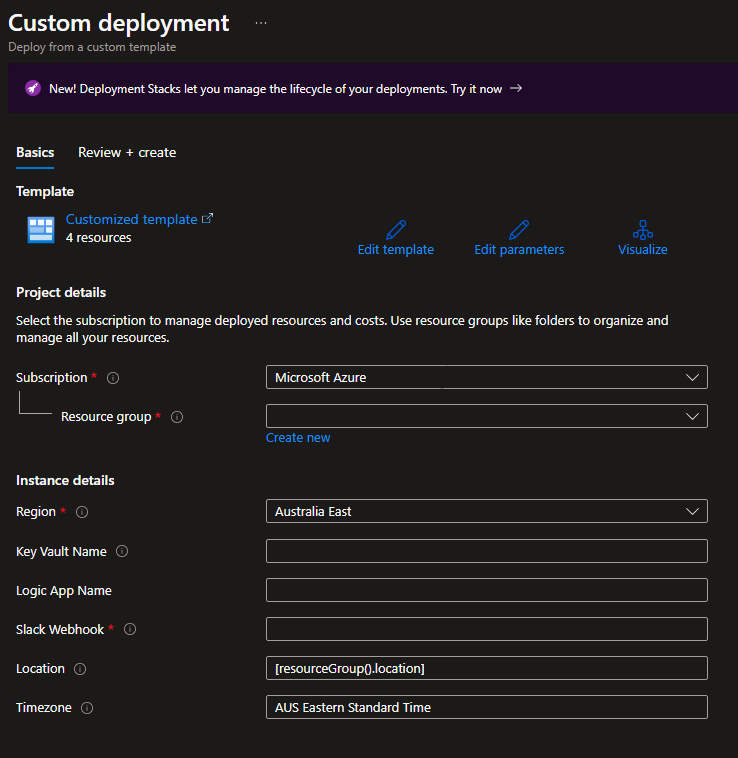
The fields Subscription, Resource group and Region are Azure wide and should be filled according to where you want to deploy the resources.
- Key Vault Name = is the name of the key vault (keep in mind the names are up to 24 characters and need to be globally unique)
- Logic App Name = is the name of the logic app (make sure you take note of that as it will be required in the next steps)
- Slack / Teams Weboook = the link for the webhook of you IM solution (if you are unsure how to create those check below).
- Timezone = Graph API localize all timestamps to UTC, so this will allow you to use a conversion to a preferred timezone (please refer to [this list][timezone]{:target=”_blank”})
Delegating Permissions
Managed Identity Permission Delegation
Your logic app needs read access to a Graph scope, so it can read Audit logs.
Install-Module Microsoft.Graph -Force -AllowClobber
Connect-MgGraph -Scopes Application.Read.All, AppRoleAssignment.ReadWrite.All
$MI = "LOGICAPP_NAMER_OR_ID"
$roleName = @("AuditLog.Read.All")
$MIID = if (!([guid]::TryParse("$MI", $([ref][guid]::Empty)))) {Get-MgServicePrincipal -Filter "DisplayName eq '$MI'"} else{Get-MgServicePrincipal -ServicePrincipalId $MI}
$msgraph = Get-MgServicePrincipal -Filter "AppId eq '00000003-0000-0000-c000-000000000000'"
foreach ($role in $roleName)
{
$role = $Msgraph.AppRoles| Where-Object {$_.Value -eq $role}
New-MgServicePrincipalAppRoleAssignment -ServicePrincipalId $MIID.id -PrincipalId $MIID.id -ResourceId $msgraph.Id -AppRoleId $role.Id
}
Disconnect-MgGraph
Creating webhooks
The following icons are direct links for the documentation on how to create webhooks on teams or slack.
 |
 |
|---|---|
| TEAMS | SLACK |
Enable Logic App
Once the steps above are completed you can now Enable the logic app from its main page.
Alert Examples
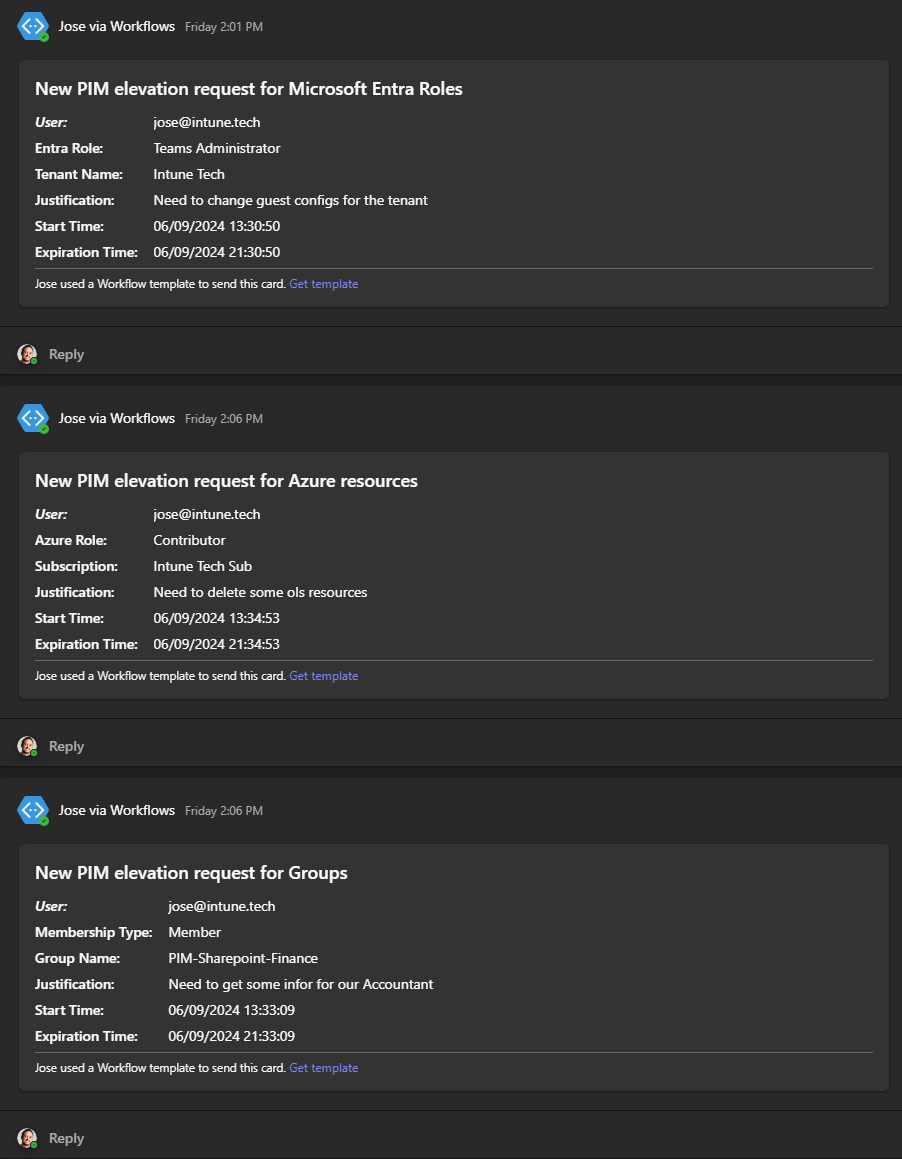
Teams notification example for PIM elevation requests
Slack notification example for PIM elevation requests
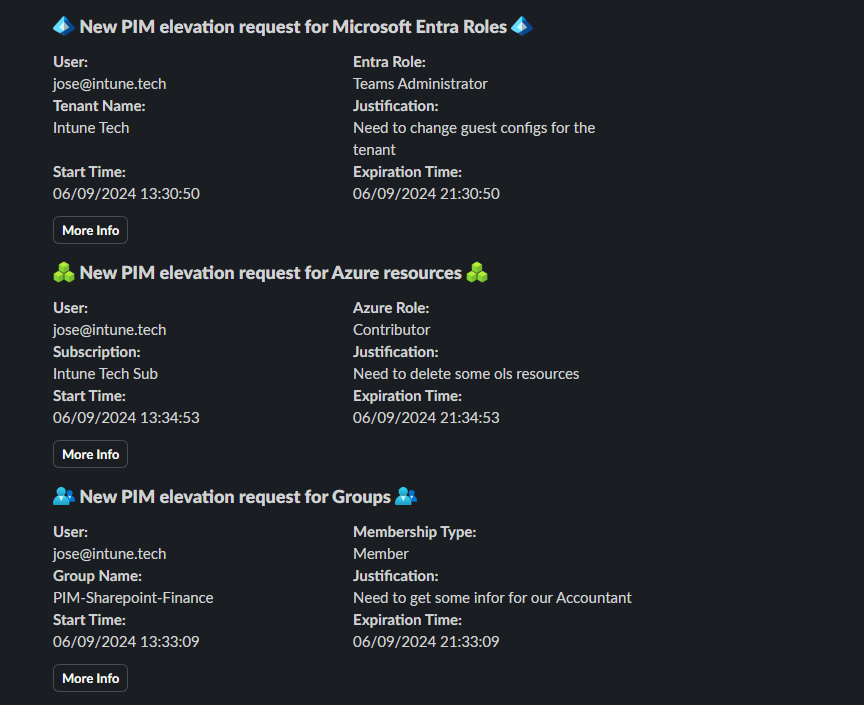
Thanks for reading and I hope these logic apps can help you monitor your PIM elevation requests.
Comments