
Introduction
While attending Workkplace Ninja Summit 2023 a couple weeks ago I attended a great session by Aria Carley, Ken Goossens and team where they walked us through “The ultimate update troubleshooting & live debugging session”. On that session I learned about a tool Microsoft created to help admins on collecting logs to troubleshoot endpoints updates. It is available here. The tool requires elevated privilges to run and presents some quirkness when silently running it, so this blog post will cover how to leverage Intune to generate those logs client side and then collect them to a central location without requiring any end user interaction.
Componenets
This solution will be using a Win32App composed of the tool and a wrapper script which will run the tool (copylogs.exe) and move the logs to a specified location. Two options are provided, which will be discussed below.
Option 1
If only a handfull of devices need to collect the data, Option1 should be used, which move the logs to C:\ProgramData\Microsoft\IntuneManagementExtension\Logs. After the logs are generated, a simple Intune device “Collect diagnostics” action should fetch the logs and make them available inside folder (62) FoldersFiles ProgramData_Microsoft_IntuneManagementExtension_Logs of the device diagnostics. If unsure how to do that, please visit Collect diagnostics
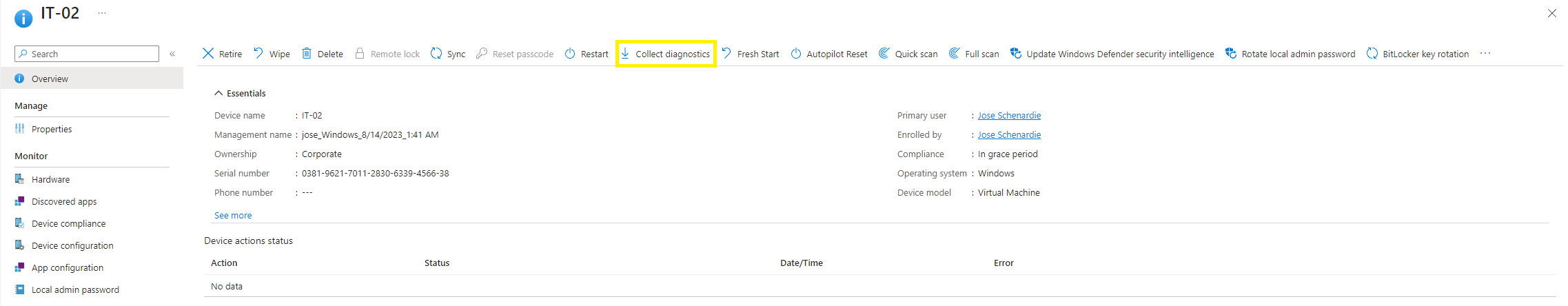
To facilitate deployment, Option1.intunewin was made available and can be deployed as a Win32App with the following configs:
| Name | Collect Windows Updates Troubleshooting Logs |
| Description | This application will collect Windows Updates troubleshooting logs and output the compressed folder to C:\ProgramData\Microsoft\IntuneManagementExtension\Logs |
| Publisher | Intune.Tech |
| Install command | %windir%\sysnative\windowspowershell\v1.0\powershell.exe -executionPolicy bypass -windowstyle hidden -file “./Install.ps1” |
| Uninstall command | %windir%\sysnative\windowspowershell\v1.0\powershell.exe -command “Remove-Item C:\PROGRAMDATA\Microsoft\IntuneManagementExtension\Logs\WindowsUpdateLogs.zip -Force” |
| Detection rules - Rule Type | File |
| Detection rules - Path | %PROGRAMDATA%\Microsoft\IntuneManagementExtension\Logs |
| Detection rules - File or folder | WindowsUpdateLogs.zip |
| Detection rules - Detection method | File or folder exists |
Option 2
If many devices are required to collect logs, going to the portal, initiating collection, downloading and collating them becomes a tedius, time consuming task. For those, Option2 should be used, which will move the logs to C:\Windows\Temp. Once done, a new configuration profile will be required to perform centralised collection of the logs using Diagnostic Log CSP, an Azure subcription with a Storage account configured.
To facilitate deployment, Option2.intunewin was made available and can be deployed as a Win32App with the following configs:
| Name | Collect Windows Updates Troubleshooting Logs |
| Description | This application will collect Windows Updates troubleshooting logs and output the compressed folder to C:\Windows\Temp |
| Publisher | Intune.Tech |
| Install command | %windir%\sysnative\windowspowershell\v1.0\powershell.exe -executionPolicy bypass -windowstyle hidden -file “./Install.ps1” |
| Uninstall command | %windir%\sysnative\windowspowershell\v1.0\powershell.exe -command “Remove-Item C:\Windows\Temp\WindowsUpdateLogs.zip -Force” |
| Detection rules - Rule Type | File |
| Detection rules - Path | %WINDIR%\Temp |
| Detection rules - File or folder | WindowsUpdateLogs.zip |
| Detection rules - Detection method | File or folder exists |
Once the Azure subscription with an storage account is created, navigate to the storage accounts and create a new container:
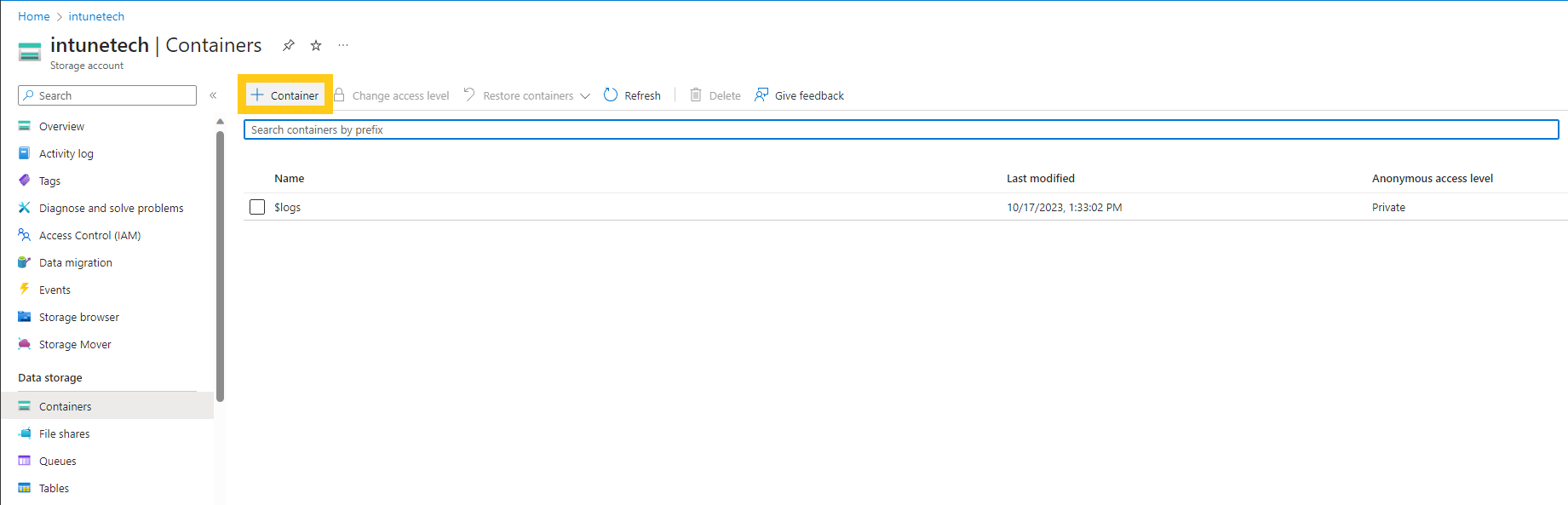
Then navigate to the created container and Shared access tokens, where a shared access token with create permissions only should be created. Also make sure to give enough time for the token before it’s expiry date so the logs cant actually be copied (after expiry date the token will be invalidated and no new files can be added to the storage account).
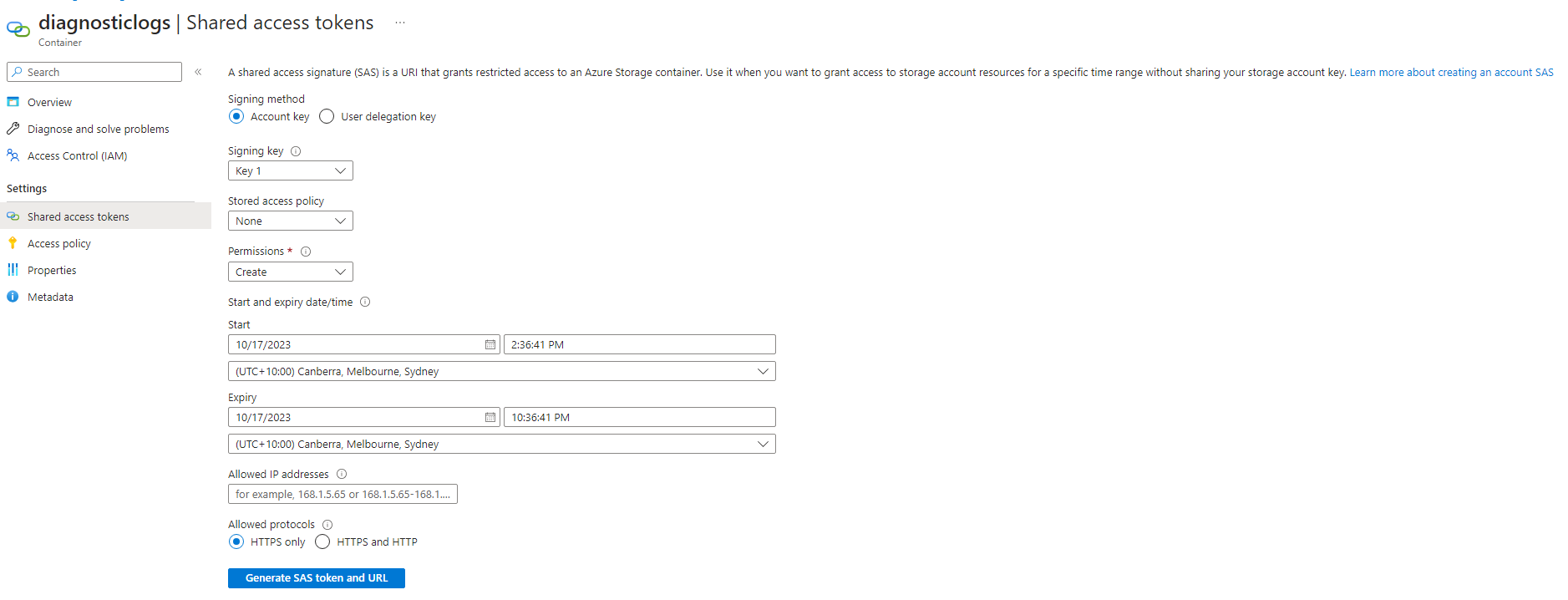
Once done, click Generate SAS token and URL and save the Blob SAS URL as it will be used by Diagnostics CSP.
The last step will be creating the configuration profile and assigning to all required devices. On Intune console, go to Devices > Configuration profiles > Create profile, then select Windows 10 and later > Templates > Custom > Create
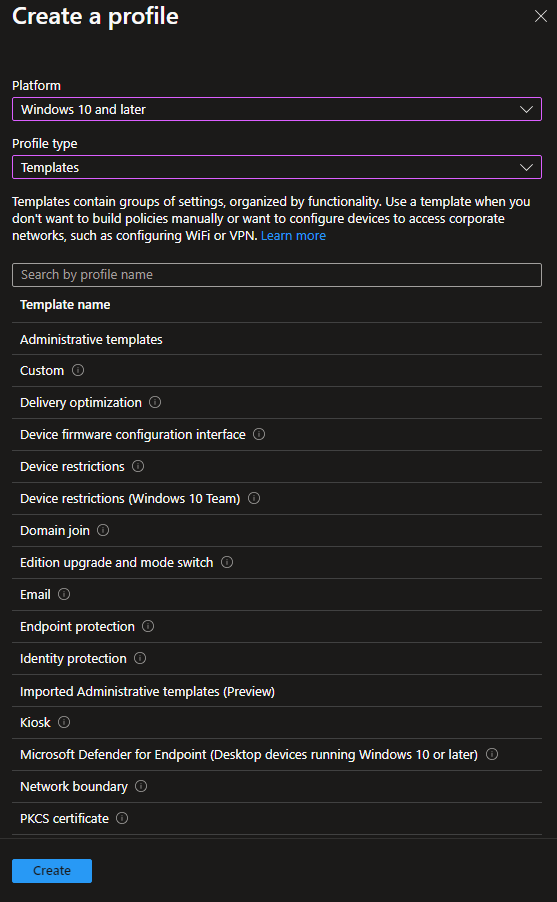
Add the following OMA-URI Setting replacing the Blob SAS URL from the one saved above.
| Name | Diagnostic Log |
| OMA-URI | ./Vendor/MSFT/DiagnosticLog/DiagnosticArchive/ArchiveDefinition |
| Data type | String |
| Value | <Collection> <ID>cb0b6c3c-8ef1-4833-a92e-f57d8ee1e06b</ID> <SasUrl><![CDATA[Blob SAS URL]]></SasUrl> <FoldersFiles>C:\Windows\Temp\WindowsUpdateLogs.zip</FoldersFiles> </Collection> |
Note: Once this custom profile is assigned it will run the collection only once, despite the log folder being there or not, so make sure the Win32App is assigned and has enough time to generate the logs before trying to collect them. Optionally change the GUID under Collection ID to force re-collection on all assigned devices.
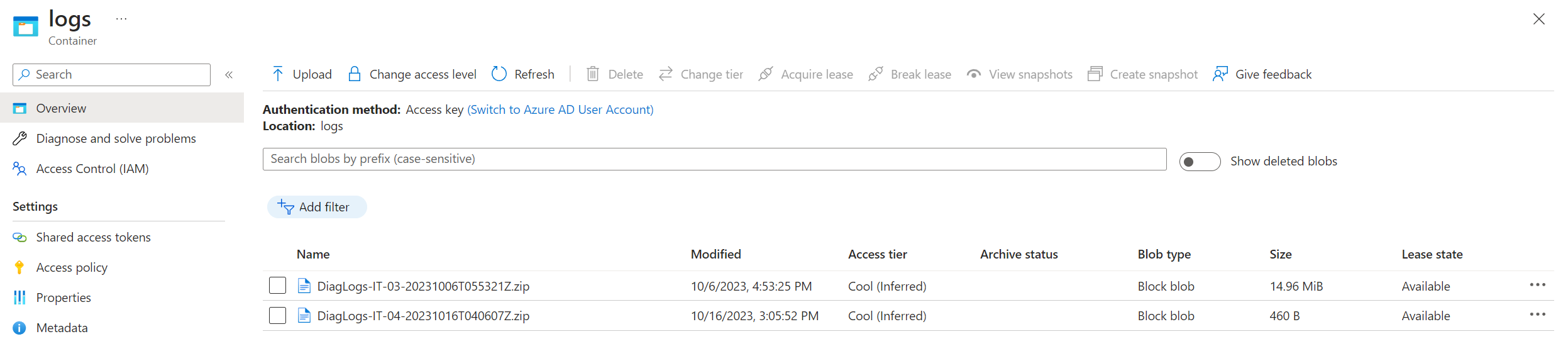
In this example the collection happened on IT-03 and IT-04, but the logs weren’t generated by the time the collection happened on IT-04, resulting on a collection with 460b instead the almost 15mbs on IT-03. To avoid such scenario, dont assign both the app and configuration profile to the same group, or at least not at the same time.
Hope that was informative and thanks for reading.
Comments